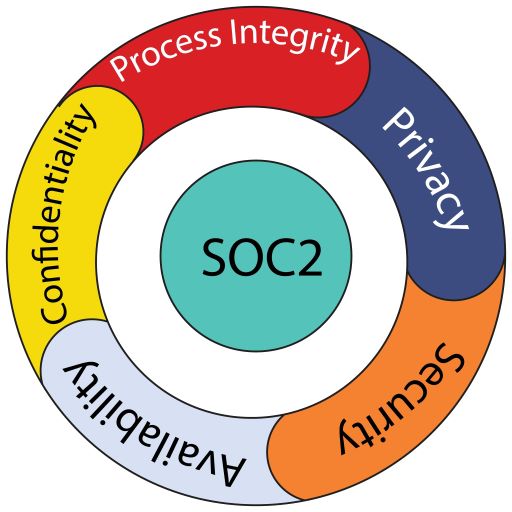
SOC 2 Trust Services Principles
In today’s interconnected and data-driven world, maintaining trust in the security and privacy of sensitive information is paramount. As organizations increasingly rely on third-party service providers to handle their data, it becomes crucial to ensure that these providers meet the highest standards of security and integrity. This is where SOC 2 (Service Organization Control 2) […]