In today’s digital age, organizations face an ever-increasing number of security threats. Protecting sensitive information and maintaining the trust of customers and stakeholders has become critical aspect of any business operation. This is where the Information Security Management System (ISMS) framework comes into play. In this article, we will explore the ISMS framework, its benefits, and its components, and provide a step-by-step guide to implementing it successfully.
Contents
Introduction
In a world driven by data and technology, organizations must adopt proactive measures to secure their valuable assets. The ISMS framework serves as a structured approach to managing information security risks effectively. It provides a systematic framework that enables organizations to identify, assess, and manage security vulnerabilities and protect sensitive information from unauthorized access, disclosure, alteration, and destruction.
What is the ISMS Framework?
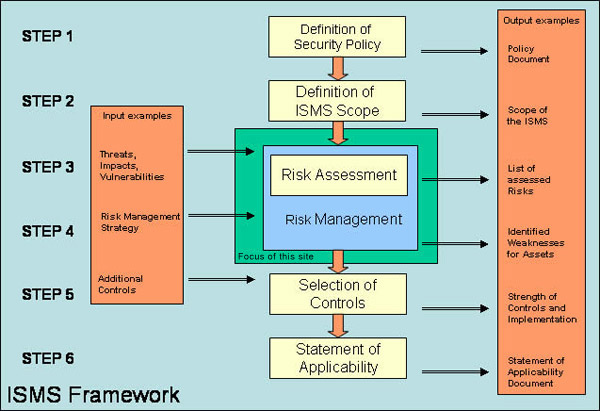
The ISMS framework refers to the Information Security Management System framework. It is a systematic approach used by organizations to manage and protect their information assets. The framework provides a structured set of policies, processes, procedures, and controls that are implemented to manage risks and ensure the confidentiality, integrity, and availability of an organization’s information.
The ISMS framework is commonly based on international standards such as ISO/IEC 27001:2013 (ISO 27001) and ISO/IEC 27002:2013 (ISO 27002). These standards guide establishing, implementing, maintaining, and continually improving an information security management system.
Benefits of Implementing the ISMS Framework
Implementing the ISMS framework brings several benefits to organizations:
- Enhanced Security: The ISMS framework helps organizations identify and address security vulnerabilities, reducing the risk of data breaches, cyber-attacks, and other security incidents.
- Compliance with Regulations: The framework enables organizations to meet regulatory and legal requirements related to information security, such as the General Data Protection Regulation (GDPR) or industry-specific standards.
- Improved Stakeholder Confidence: Implementing the ISMS framework demonstrates a commitment to protecting sensitive information, and enhancing trust among customers, partners, and stakeholders.
- Efficient Resource Allocation: The framework enables organizations to prioritize their security efforts and allocate resources effectively to address the most critical risks.
Components of the ISMS Framework
The ISMS framework comprises several key components that work together to ensure comprehensive information security management:
- Information Security Policy: This document outlines the organization’s commitment to information security and provides a high-level overview of security objectives and responsibilities.
- Risk Assessment and Management: Organizations perform risk assessments to identify and evaluate potential security threats, enabling them to develop appropriate controls and mitigation strategies.
- Asset Management: This component involves identifying and classifying information assets based on their importance and implementing appropriate safeguards to protect them.
- Access Control: Access control mechanisms are put in place to ensure that only authorized individuals have access to sensitive information, minimizing the risk of unauthorized disclosure or data breaches.
- Incident Response: The framework includes processes and procedures to effectively respond to and manage security incidents, minimizing their impact and facilitating swift recovery.
- Monitoring and Review: Regular monitoring and review of security controls, policies, and procedures are essential to identify vulnerabilities and ensure ongoing compliance with the framework.
Step-by-Step Guide to Implementing the ISMS Framework

Implementing the ISMS framework requires a structured approach. Here is a step-by-step guide to help organizations successfully implement the framework:
Define the Scope and Objectives
Start by defining the scope of the ISMS framework implementation. Identify the areas of the organization that will be covered and set clear objectives for the implementation process. This step ensures that everyone involved understands the purpose and extent of the framework.
Conduct Risk Assessment
Perform a thorough risk assessment to identify potential security threats and vulnerabilities. This assessment should include an evaluation of the organization’s assets, potential risks, and the likelihood and impact of those risks. The findings will serve as a basis for developing appropriate controls and mitigation strategies.
Develop Policies and Procedures
Develop comprehensive information security policies and procedures based on the identified risks and objectives. These policies should outline the organization’s approach to information security, including areas such as data classification, access control, incident response, and employee awareness. Clearly define roles and responsibilities for implementing and maintaining these policies.
Implement Controls
Implement appropriate controls to mitigate the identified risks. This may include technical measures such as firewalls, encryption, and access controls, as well as administrative measures such as training programs, awareness campaigns, and incident reporting mechanisms. Regularly review and update these controls to adapt to evolving threats.
Monitor and Review
Establish mechanisms for ongoing monitoring and review of the implemented controls. Regularly assess the effectiveness of the controls and identify any gaps or areas for improvement. This includes conducting internal audits, penetration testing, and vulnerability assessments to ensure compliance with the framework and identify potential weaknesses.
Continual Improvement
The ISMS framework is an ongoing process that requires continual improvement. Actively seek feedback from employees and stakeholders, and incorporate lessons learned from security incidents or emerging threats. Continuously refine and enhance the framework to adapt to changes in technology, regulations, and the organizational landscape.
Challenges in Implementing the ISMS Framework
Implementing the ISMS framework can pose certain challenges that organizations need to be aware of and address:
- Organizational Resistance: Resistance to change and lack of awareness among employees can hinder the successful implementation of the framework. Effective communication, training programs, and stakeholder involvement can help overcome these challenges.
- Resource Constraints: Implementing and maintaining the ISMS framework requires dedicated resources, both in terms of personnel and financial investment. Organizations need to allocate sufficient resources to ensure the framework’s effectiveness.
- Complexity: The ISMS framework can be complex, especially for organizations with diverse operations and information systems. Clear documentation, guidance, and support from information security professionals can help navigate the complexity.
Uses for Successful Implementation

To ensure the successful implementation of the ISMS framework, consider the following best practices:
- Top-Down Approach: Obtain leadership support and commitment to information security initiatives. Leadership buy-in helps foster a culture of security throughout the organization.
- Engage Stakeholders: Involve stakeholders from different departments and levels of the organization in the implementation process. This ensures a comprehensive understanding of information security requirements and increases ownership.
- Training and Awareness: Provide regular training and awareness programs to employees to educate them about information security policies, procedures, and responsibilities. This helps create a security-conscious workforce.
- Regular Audits and Assessments: Conduct periodic audits and assessments to evaluate the effectiveness of the implemented controls and identify areas for improvement. This helps maintain compliance and address emerging risks.
- Stay Updated: Stay abreast of emerging threats, industry best practices, and changes in regulations. Regularly update the ISMS framework to incorporate new knowledge and technologies.
Conclusion
In an increasingly digital world, implementing the ISMS framework is crucial for organizations to effectively manage information security risks. The framework provides a structured approach to identify, assess, and mitigate security vulnerabilities, ensuring the confidentiality, integrity, and availability of valuable information assets.
In conclusion, the ISMS framework serves as a vital tool for organizations to safeguard their sensitive information, protect against security threats, and build trust with customers and stakeholders. By embracing the framework and following the recommended guidelines, organizations can establish a robust information security management system. It aligns with industry best practices and regulatory requirements.
If you are looking to implement any of the Infosec compliance frameworks such as SOC 2 compliance, HIPAA, ISO 27001, and GDPR compliance, Impanix can help. Book a Free consultation call with our experts or email us at [email protected] for inquiries.