In today’s digital age, information security is of paramount importance for businesses of all sizes. The risk of data breaches, cyberattacks, and unauthorized access to sensitive information continues to rise. To address these concerns, organizations are turning to international standards such as ISO 27001 to establish robust information security management systems. This article will provide a comprehensive overview of ISO 27001 information security, its benefits, and the process of implementation.
Contents
Introduction to ISO 27001 Information Security

ISO 27001 is an international standard for information security management systems (ISMS). It provides a systematic approach to managing sensitive company information, ensuring its confidentiality, integrity, and availability. ISO 27001 sets out the criteria for establishing, implementing, maintaining, and continually improving an ISMS within the context of an organization’s overall business risks.
The goal of ISO 27001 is to help organizations protect their information assets and establish a robust framework for managing security risks. By implementing the standard, organizations can identify and address potential security vulnerabilities, enhance their security posture, and gain confidence from customers, partners, and stakeholders that their information is being handled securely.
Understanding the Importance of Information Security
Effective information security measures are crucial for businesses to protect the confidentiality, integrity, and availability of their sensitive data. By implementing ISO 27001, organizations demonstrate their commitment to safeguarding information assets and ensuring customer trust. ISO 27001 provides a framework that helps organizations identify and address potential risks while complying with legal and regulatory requirements.
ISO 27001 certification is an official recognition that an organization has successfully implemented an ISMS by the requirements of the standard. It involves a rigorous assessment by an independent certification body to ensure compliance with ISO 27001’s controls and processes. Achieving certification provides several benefits, including enhanced credibility, improved risk management, and a competitive advantage in the marketplace.
Key Elements of ISO 27001 Information Security

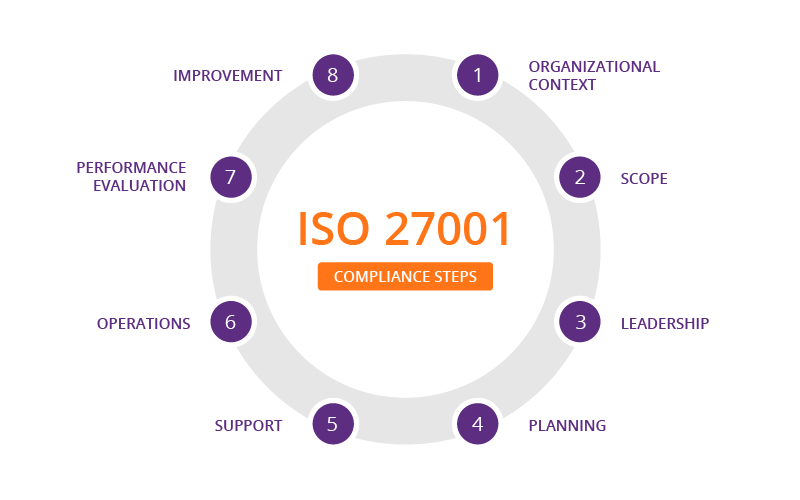
The implementation of ISO 27001 revolves around several key elements that form the foundation of an effective ISMS:
Risk Assessment and Management
Before implementing security controls, organizations must identify and assess potential risks to their information assets. This involves evaluating vulnerabilities, threats, and the potential impact of security incidents. Based on the risk assessment, appropriate risk treatment plans are developed to mitigate identified risks.
Information Security Policies and Procedures
ISO 27001 emphasizes the need for well-defined information security policies and procedures. These policies outline the organization’s commitment to information security and guide how to handle various security-related aspects. Procedures ensure that security measures are implemented consistently throughout the organization.
Training and Awareness Programs
Employees play a crucial role in ensuring information security. ISO 27001 encourages organizations to provide training and awareness programs to educate employees about their roles and responsibilities in protecting sensitive information. Such programs help foster a culture of security awareness and ensure employees are equipped to handle security incidents effectively.
Incident Response and Business Continuity Planning
ISO 27001 emphasizes the need for organizations to have robust incident response and business continuity plans. These plans define the steps to be taken in the event of a security incident or disruption to business operations. They outline procedures for reporting, investigating, and resolving incidents, as well as strategies for maintaining critical business functions during and after disruptive events.
Monitoring and Reviewing of Controls
ISO 27001 requires organizations to establish processes for monitoring, reviewing, and continuously improving their information security controls. Regular assessments and audits help identify any gaps or weaknesses in the implemented controls, allowing organizations to take corrective actions and ensure the effectiveness of their security measures.
Implementing ISO 27001 in an Organization

Implementing ISO 27001 requires a systematic approach and involves several stages:
Establishing the Information Security Management System (ISMS)
The first step is to establish an ISMS within the organization. This involves defining the scope of the system, identifying stakeholders, and appointing a management representative responsible for overseeing the implementation process.
Conducting Gap Analysis and Risk Assessment
A comprehensive gap analysis is conducted to identify the organization’s existing information security practices and any gaps in ISO 27001 requirements. Following this, a detailed risk assessment is performed to identify and assess the risks associated with the organization’s information assets.
Developing and Implementing Security Controls
Based on the identified risks, the organization develops and implements appropriate security controls to mitigate those risks. These controls can include technical measures, policies and procedures, access controls, encryption, and regular security awareness training.
Conducting Internal Audits
Internal audits are conducted to evaluate the effectiveness of the implemented controls and ensure compliance with ISO 27001 requirements. Audits help identify areas for improvement and provide an opportunity to refine the ISMS further.
Management Review and Certification Process
Once the ISMS has been implemented and internal audits have been conducted, a management review takes place to assess the overall performance of the system. Following this, the organization can engage an independent certification body to perform an external audit for ISO 27001 certification.
Challenges and Considerations in ISO 27001 Implementation

Implementing ISO 27001 can pose certain challenges and considerations for organizations:
Resource Allocation and Budgeting
Implementing and maintaining an effective ISMS requires dedicated resources, including skilled personnel, time, and financial investments. Organizations need to allocate sufficient resources and budget to ensure the successful implementation and ongoing management of ISO 27001.
Employee Resistance to Change
Implementing ISO 27001 often requires changes in processes, policies, and employee behaviors. Resistance to change can hinder the implementation process. It is essential to communicate the benefits of ISO 27001 to employees and provide training and support to ensure their active participation and cooperation.
Integration with Existing Processes
Organizations need to integrate ISO 27001 requirements seamlessly into their existing processes and procedures. This requires careful planning and coordination to avoid disruption to ongoing operations while ensuring compliance with the standard.
Conclusion
ISO 27001 provides a robust framework for organizations to establish and maintain effective information security management systems. By implementing ISO 27001, businesses can enhance their ability to protect sensitive information, mitigate risks, and comply with legal and regulatory requirements. However, successful implementation requires careful planning, resource allocation, and employee engagement. By following the steps outlined in this article, organizations can navigate the process of ISO 27001 implementation and strengthen their overall information security posture.
If you are looking to implement any of the Infosec compliance frameworks such as SOC 2 compliance, HIPAA, ISO 27001, and GDPR compliance, Impanix can help. Book a Free consultation call with our experts or email us at [email protected] for inquiries