The digital landscape is continually evolving, bringing both opportunities and challenges for organizations worldwide. With the increasing frequency and sophistication of cyber threats, it has become imperative for businesses to prioritize cybersecurity and establish robust frameworks to protect their sensitive data and critical infrastructure. In this article, we will delve into the National Institute of Standards and Technology (NIST) Cybersecurity Framework (CSF), a comprehensive and widely recognized approach that helps organizations effectively manage and mitigate cyber risks.
Contents
- 1 Importance of Cybersecurity Framework
- 2 What is the NIST Cybersecurity Framework?
- 3 Benefits of Adopting the Framework
- 4 Core Functions of the NIST CSF
- 5 Implementing the NIST CSF
- 6 Integrating the NIST Cybersecurity Framework (CSF) into Organizational Culture
- 7 Industry Adoption of the NIST Cybersecurity Framework (CSF)
- 8 Addressing Challenges and Limitations
- 9 Conclusion
Importance of Cybersecurity Framework
In today’s interconnected world, organizations of all sizes and industries face an ever-expanding range of cyber threats. A cybersecurity framework, such as the one provided by NIST, offers a structured approach to identify, protect, detect, respond to, and recover from these threats. By implementing the NIST CSF, organizations can fortify their cybersecurity posture, effectively safeguard their assets, and maintain the trust of their stakeholders.
What is the NIST Cybersecurity Framework?
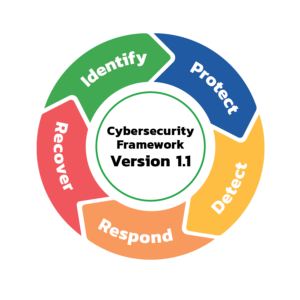
The NIST CSF consists of a set of guidelines, best practices, and standards that enable organizations to manage and mitigate cyber risks. It provides a common language and framework that organizations can use to assess and improve their cybersecurity capabilities. The framework comprises five core functions: Identity, Protect, Detect, Respond, and Recover.
NIST stands for National Institute of Standards and Technology, a non-regulatory federal agency under the United States Department of Commerce, that plays a vital role in developing and promoting standards, guidelines, and best practices for various sectors. NIST’s expertise extends to cybersecurity, where it provides valuable resources to help organizations enhance their cyber resilience.
Benefits of Adopting the Framework
Implementing the NIST CSF offers several benefits to organizations:
- Risk-based approach: The framework helps organizations prioritize their cybersecurity efforts based on their unique risk profiles, ensuring efficient resource allocation.
- Common language: The NIST CSF provides a common language and set of practices that enable effective communication and collaboration among internal teams, external partners, and regulators.
- Flexibility: The framework is flexible and scalable, accommodating organizations of all sizes and industries. It allows customization based on specific needs and risk tolerances.
- Regulatory compliance: Many regulatory bodies, both in the United States and internationally, recognize and recommend the NIST CSF as a valuable framework for meeting compliance requirements.
- Enhanced resilience: By following the framework’s principles, organizations can proactively identify and address vulnerabilities, minimizing the likelihood and impact of cyber incidents.
Core Functions of the NIST CSF

These are some of the core functions of the NIST CSF framework:
Identify
The first core function, Identity, focuses on understanding and managing cybersecurity risks. This involves identifying and documenting critical assets, assessing vulnerabilities, and understanding the potential impact of cyber threats. By conducting comprehensive risk assessments, organizations gain valuable insights that drive informed decision-making and resource allocation.
Protect
The Protect function involves implementing safeguards to ensure the security and integrity of critical assets. This includes activities such as access control, data encryption, secure configuration management, and regular security awareness training for employees. By establishing strong protective measures, organizations can prevent or minimize the impact of potential cyber incidents.
Detect
The Detect function emphasizes continuous monitoring and timely detection of cybersecurity events. This includes activities like intrusion detection systems, log analysis, threat intelligence gathering, and establishing incident response mechanisms. Rapid detection enables organizations to swiftly respond and mitigate the impact of incidents, minimizing potential damages.
Respond
The Respond function focuses on taking immediate action when a cybersecurity incident occurs. This includes developing an incident response plan, establishing communication channels, and coordinating activities to contain and eradicate the incident. Responding effectively and efficiently helps organizations minimize the disruption caused by incidents and facilitate a swift recovery.
Recover
The Recover function involves restoring normal operations after a cybersecurity incident. This includes assessing the damage, implementing recovery plans, and conducting lessons-learned exercises to improve future incident response. By efficiently recovering from incidents, organizations can reduce downtime, restore trust, and strengthen their overall resilience.
Implementing the NIST CSF
Implementing the NIST CSF involves several key steps:
Assessing Current Cybersecurity Posture
Before implementing the framework, organizations should conduct a thorough assessment of their current cybersecurity posture. This includes identifying strengths, weaknesses, and gaps in their security measures. By understanding their starting point, organizations can develop targeted strategies for improvement.
Creating a Roadmap for Implementation
Based on the assessment, organizations should create a roadmap that outlines the specific actions and initiatives required to implement the NIST CSF. The roadmap should prioritize critical areas and align with the organization’s risk appetite and available resources.
Executing the Implementation Plan
With the roadmap in place, organizations can begin executing the implementation plan. This involves deploying security controls, enhancing employee awareness and training, integrating security into business processes, and establishing metrics to measure progress.
Integrating the NIST Cybersecurity Framework (CSF) into Organizational Culture
For successful implementation and long-term effectiveness, organizations need to integrate the NIST CSF into their organizational culture. This requires concerted effort and commitment from leadership, active employee engagement, and a continuous improvement mindset.
Leadership Commitment
Leadership plays a crucial role in driving the adoption and integration of the NIST CSF. Executives and managers should demonstrate a commitment to cybersecurity by allocating resources, setting clear expectations, and actively participating in cybersecurity initiatives. Their visible support sets the tone for the entire organization and reinforces the importance of cybersecurity.
Employee Engagement and Awareness
Engaging employees and fostering a culture of cybersecurity awareness are essential. Regular training and awareness programs should be conducted to educate employees about the risks, best practices, and their responsibilities in maintaining a secure environment. Employees should be encouraged to report potential threats and actively participate in cybersecurity initiatives.
Continuous Improvement and Evaluation
The NIST CSF is not a one-time implementation but an ongoing process. Organizations should regularly assess their cybersecurity posture, identify areas for improvement, and update their strategies accordingly. Continuous monitoring, periodic audits, and vulnerability assessments are essential to adapt to the evolving threat landscape and maintain a robust security framework.
Industry Adoption of the NIST Cybersecurity Framework (CSF)

The NIST CSF has gained significant traction across industries due to its effectiveness and flexibility. Many organizations, ranging from small businesses to large enterprises, have successfully adopted the framework and achieved improved cybersecurity resilience.
Success Stories and Case Studies
Numerous success stories highlight the benefits of implementing the NIST CSF. Organizations that have embraced the framework have witnessed reduced cybersecurity incidents, minimized financial losses, enhanced customer trust, and improved overall business performance. Case studies demonstrating the successful implementation of the NIST CSF serve as valuable references for other organizations seeking to enhance their cybersecurity posture.
Government and Regulatory Support
Government agencies and regulatory bodies worldwide have recognized the value of the NIST CSF and incorporated it into their guidelines and frameworks. Compliance with the NIST CSF often helps organizations meet regulatory requirements and demonstrates a commitment to robust cybersecurity practices. The support and endorsement from government entities further encourage organizations to adopt the framework.
Addressing Challenges and Limitations
While the NIST CSF offers numerous benefits, organizations may encounter challenges during implementation. It is important to acknowledge and address these challenges effectively.
Complexity and Customization
The NIST CSF is a comprehensive framework, and organizations may find it complex to navigate and customize according to their specific needs. It requires a thorough understanding of the framework’s components and tailoring them to align with the organization’s objectives and risk appetite. Seeking expert guidance and leveraging available resources can help simplify the implementation process.
Resource Constraints
Implementing and maintaining a robust cybersecurity framework requires adequate resources, including financial investments, skilled personnel, and advanced technologies. Smaller organizations with limited budgets and manpower may face challenges in allocating resources for cybersecurity initiatives. However, prioritizing critical areas, leveraging cost-effective solutions, and seeking external support can help mitigate these constraints.
Evolving Threat Landscape
Cyber threats are constantly evolving, requiring organizations to remain vigilant and adapt their cybersecurity strategies accordingly. The NIST CSF provides a solid foundation, but organizations must continually monitor emerging threats, stay updated on industry trends, and proactively adjust their security measures to effectively counter new risks.
Conclusion
In today’s digital age, organizations must prioritize cybersecurity to protect their assets, maintain trust, and ensure business continuity. The NIST Cybersecurity Framework (CSF) offers a comprehensive approach to managing and mitigating cyber risks. By implementing the NIST CSF, organizations can enhance their cybersecurity posture, establish effective safeguards, and respond efficiently to potential incidents.
The framework’s flexibility, industry acceptance, and government support make it a valuable tool for organizations across sectors. By integrating the NIST CSF into their culture and embracing a continuous improvement mindset, organizations can proactively address cyber threats and foster resilient cybersecurity practices.
If you are looking to implement any of the Infosec compliance frameworks such as SOC 2 compliance, HIPAA, ISO 27001, and GDPR compliance, Impanix can help. Book a Free consultation call with our experts or email us at [email protected] for inquiries.
Read Related Blogs
