Amidst the vast landscape of cybersecurity, one concept stands at the forefront of safeguarding our data: Penetration Testing. As the name suggests, it involves an authorized simulated cyber-attack on a computer system. That aimed at assessing its vulnerabilities which could be exploited by hackers. This blog will delve into the intricate details of penetration testing, its significance, and the role it plays in strengthening the digital fortress of your business.
Contents
What Is Penetration Testing With Example?
 Penetration testing is also known as ethical hacking. It is a practice used by cybersecurity professionals to identify and evaluate potential vulnerabilities in a network, system, or web application. The goal of penetration testing is to proactively identify weaknesses before malicious actors such as hackers, exploit them. Thereby preventing data breaches and maintaining the integrity and confidentiality of the system.
Penetration testing is also known as ethical hacking. It is a practice used by cybersecurity professionals to identify and evaluate potential vulnerabilities in a network, system, or web application. The goal of penetration testing is to proactively identify weaknesses before malicious actors such as hackers, exploit them. Thereby preventing data breaches and maintaining the integrity and confidentiality of the system.
To further illustrate, let’s consider an example.
Imagine a major bank, Bank XYZ, serve thousands of customers and handle a tremendous amount of sensitive data every day. The exposure of any such data could lead to severe consequences, both financially and reputationally.
To ensure the security of its digital systems, Bank XYZ employs a team of ethical hackers to conduct a penetration test. This team, after obtaining necessary permissions, will simulate a cyber attack on the bank’s digital infrastructure. They may start with something as simple as a phishing attack. After the penetration test, the team will provide a detailed report to the bank, outlining the vulnerabilities they exploited, the data they could access, and how long it took them to break into the system.
Later, by understanding and addressing these vulnerabilities, Bank XYZ can improve its defenses, better protect its sensitive data. And eventually, reduce the risk of a real cyber attack.
How Is Penetration Testing And Real-World Cyber Attacks Differs?
While penetration testing and real-world cyber attacks may appear similar in their methods and techniques. But, there are fundamental differences between the two in terms of their purpose, legality, and impact.
Purpose
The primary difference lies in the intent behind the actions. Penetration testing, or ethical hacking, is conducted with the goal of identifying and fixing vulnerabilities in a system or network, enhancing its overall security. Real-world cyber attacks, on the other hand, are intended to exploit vulnerabilities, cause harm, and often, gain unauthorized access to sensitive data for malicious purposes like theft, ransom, or disruption of services.
Legality
Penetration testing is a legal activity. Ethical hackers are authorized professionals who have been granted explicit permission to conduct tests on the specified systems. Real-world cyber attacks are illegal activities conducted by cybercriminals without any permission.
Consent
Prior to a penetration test, an agreement is typically made that outlines the scope of the test, the systems to be tested, the methods to be used, and the times at which testing will occur. Real-world cyber attacks are unsolicited, with cybercriminals often working to remain undetected for as long as possible.
Impact
The impact of a penetration test is controlled. Ethical hackers know to avoid causing harm to the system and to minimize disruptions to normal operations. In contrast, real-world cyber attacks can cause significant damage, including data breaches, system damage, financial loss, and reputation damage.
Reporting
At the end of a penetration test, the ethical hackers will provide a detailed report of their findings, including the vulnerabilities identified and recommendations for remediation. In contrast, cybercriminals do not provide reports; their actions often only become evident after a breach has occurred.
Consequence
There is no legal consequence for the ethical hackers conducting a penetration test, as they are acting within the confines of the law. However, cybercriminals conducting illegal activities face potential legal repercussions if caught, including fines and imprisonment.
In essence, while penetration testing uses the tactics of cybercriminals, it does so with the goal of strengthening security rather than exploiting it.
What Are The Types Of Penetration Testing?
 Penetration testing can be categorized into several types based on the amount of information provided to the testers and the source from where the test originates. Here are the main types:
Penetration testing can be categorized into several types based on the amount of information provided to the testers and the source from where the test originates. Here are the main types:
Black Box Penetration Testing
In this type of testing, the testers are given no prior knowledge about the system. This simulates an attack from an outsider who has no intimate knowledge of the system. It can be time-consuming due to the lack of information but provides a real-world scenario of how an external attacker might attempt to exploit vulnerabilities.
White Box Penetration Testing
Also known as clear box testing, the testers here are provided with full information about the system including network diagrams, source code, IP addressing, etc. This type of testing is designed to perform a thorough test of all elements of the system since the tester has comprehensive knowledge. It can help uncover vulnerabilities that might not be easily found during black box testing.
Gray Box Penetration Testing
This is a hybrid approach where the testers are given partial knowledge about the system. It simulates an attack from an insider who has limited knowledge of the system. Gray box testing is beneficial because it provides a balance between the thoroughness of white box testing and the real-world scenario of black box testing.
External Penetration Testing
This test focuses on the assets of a system that are visible on the internet, such as the web application itself, company website, email and domain name servers (DNS), etc. The goal is to exploit these systems to gain access to or disrupt the internal IT infrastructure.
Internal Penetration Testing
Unlike external testing, internal tests simulate an inside attack behind the firewall by an authorized user with standard access privileges. This could be especially useful for estimating how much damage a disgruntled employee could cause.
Blind Testing
In this type, only limited information about the target is shared with the testers. This closely simulates the real-world attacks, as hackers rarely have detailed information about their targets.
Each type of penetration test is used for a specific purpose and in a specific context. The type of test to be conducted depends on the needs and security policy of the organization.
What Is The Process Of Penetration Testing?
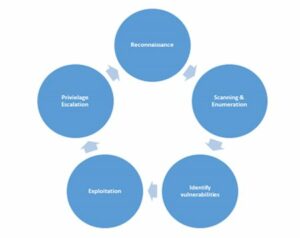 The process of penetration testing involves a set of steps that help ensure the test is comprehensive, organized, and effective. Here are the typical stages of a penetration test:
The process of penetration testing involves a set of steps that help ensure the test is comprehensive, organized, and effective. Here are the typical stages of a penetration test:
Planning and Reconnaissance
This initial phase involves defining the scope and goals of the test, including the systems to be addressed and the testing methods to be used. Reconnaissance includes gathering intelligence on the target system to understand how it operates and where it might be vulnerable. This can involve public information about the target, DNS information, domain names, mail servers, etc.
Scanning
The next step involves using automated tools to scan the target systems for vulnerabilities. This can include static analysis, where the code is reviewed to assess its behavior and find any potential weak spots, and dynamic analysis, where the system’s code is analyzed in a running state to find vulnerabilities that might not be visible in a static analysis.
Gaining Access
This phase involves using various strategies like cross-site scripting, SQL injection, and backdoor exploits to attempt to penetrate the system’s defenses. The goal is not to damage the system but to exploit any vulnerabilities found in order to gain access to data or understand what kind of damage could be inflicted.
Maintaining Access
This stage involves simulating a real-world cyber attack, where the attacker typically seeks to remain within the system undetected for as long as possible. The ethical hacker tries to create a persistent presence in the system to map the extent of the compromise that could occur.
Analysis and Reporting
The final phase involves compiling a detailed report of the vulnerabilities found, the data that was accessed, how long the penetration tester was able to remain in the system, and what potential damage could have been inflicted. The report should also include recommendations for mitigating the identified vulnerabilities and enhancing the system’s security.
Cleanup
After the test, ethical hackers or the IT team should ensure all changes made to the system are rolled back and the system is restored to its pre-testing state. This involves removing payloads, scripts, or any accounts created during the testing process.
Follow-up
This is an optional but highly recommended step that involves re-testing the system after all the identified vulnerabilities have been addressed. This ensures the vulnerabilities have been properly remediated. And no new vulnerabilities have been introduced during the remediation process.
It’s important to note that the process of penetration testing should be conducted in a controlled and careful manner. Along with explicit permission from the organization, to avoid any unintended negative consequences.
Conclusion
In conclusion, penetration testing is a critical aspect of a robust cybersecurity strategy. This proactive approach, also known as ethical hacking, involves authorized professionals simulating cyber attacks on a system to identify and rectify vulnerabilities before malicious actors can exploit them. Different types of penetration tests provide various perspectives on system security. That ranges from the viewpoint of an external hacker with no system knowledge to that of an insider with full system access.
If you are looking to implement any of the Infosec compliance frameworks such as SOC 2 compliance, HIPAA, ISO 27001, and GDPR compliance, Impanix can help. Book a Free consultation call with our experts or email us at [email protected] for inquiries.
Read Related Blogs
