Blogs

What IS SOC 1 Audit? A Complete To Compliance
In an age where data is a precious commodity, the security and reliability of financial information management have become paramount. But how do you assure

A Complete Guide To The 5 Trust Services Principles
In an increasingly digital world, securing data and maintaining its integrity is paramount for businesses of all sizes. The ability to reliably safeguard sensitive information

What Is Vendor Risk Management & Why You Need To Implement It?
In today’s complex business landscape, outsourcing services to third parties or vendors have become commonplace. However, with this practice comes an array of potential risks
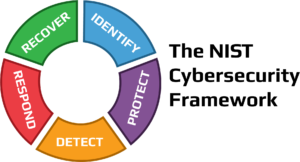
NIST Cybersecurity Framework (CSF): Enhancing Cyber Resilience
The digital landscape is continually evolving, bringing both opportunities and challenges for organizations worldwide. With the increasing frequency and sophistication of cyber threats, it has

NIST 800-53: Enhancing Cybersecurity Through
In an increasingly digital world, where the protection of sensitive information is of paramount importance, organizations must adopt robust information security practices. The National Institute

PCI Compliance for Small Business : Key Concepts and Myths
In today’s digital age, the security of sensitive customer data has become a paramount concern for businesses of all sizes. As a small business owner,

NIST vs ISO 27001 Compliance: Understanding the Differences
In today’s digital landscape, organizations face increasing cybersecurity risks and regulatory requirements. To mitigate these challenges, compliance with industry standards is essential. Two widely recognized

SOC 2 Physical Security Requirements
In today’s interconnected world, ensuring the security of sensitive information has become paramount for businesses. SOC 2 (System and Organization Controls 2) is a widely

SOC 2 Report : A Comprehensive Guide
As technology continues to advance and businesses increasingly rely on third-party service providers to handle sensitive data, the need for strong data security and privacy

SOC 2 System Description Example
In today’s digital landscape, organizations are increasingly focusing on data security, privacy, and availability. One essential tool for demonstrating their commitment to these areas is

SOC 2 Compliance: Ensuring Data Security and Trust
In today’s digital landscape, data security, and privacy have become paramount concerns for businesses. Customers expect their sensitive information to be protected from unauthorized access

SOC 2 Type 2 Principles
In today’s digital landscape, where data breaches and security incidents are becoming increasingly common, organizations must prioritize the security and privacy of their systems and