In today’s digital landscape, the security of sensitive information has become a paramount concern for businesses of all sizes. With the increasing frequency and sophistication of cyber threats, organizations must take proactive measures to safeguard their data and maintain the trust of their stakeholders. This is where the Information Security Management System (ISMS) comes into play. In this article, we will explore the importance of ISMS, its key components, implementation strategies, benefits of ISO 27001 certification, common challenges, and best practices for ISMS success.
Contents
- 1 Introduction to Information Security Management System (ISMS)
- 2 Importance of ISMS for Businesses
- 3 Key Components of an Information Security Management System (ISMS)
- 4 Implementing an Effective Information Security Management System (ISMS)
- 5 Challenges in Implementing and Maintaining ISMS
- 6 Best Practices for ISMS Success
- 7 Conclusion
Introduction to Information Security Management System (ISMS)

In the realm of cybersecurity, an ISMS refers to a systematic approach that enables organizations to manage, monitor, audit, and improve their information security practices. It provides a framework for identifying, assessing, and mitigating risks, ensuring the confidentiality, integrity, and availability of sensitive data. By implementing an ISMS, businesses can effectively protect their valuable information assets from unauthorized access, data breaches, and other security incidents.
Importance of ISMS for Businesses
These are some major uses of ISMS in businesses:
Protecting Sensitive Information
One of the primary objectives of an ISMS is to protect sensitive information from unauthorized disclosure, modification, or destruction. By implementing robust security controls and practices, organizations can ensure the confidentiality and integrity of their data. This is especially crucial for businesses that deal with personally identifiable information (PII), financial records, intellectual property, and other confidential data.
Compliance with Regulations and Standards
In today’s regulatory environment, many industries have specific requirements regarding information security. Compliance with regulations such as the General Data Protection Regulation (GDPR), Health Insurance Portability and Accountability Act (HIPAA), and Payment Card Industry Data Security Standard (PCI DSS) is mandatory for organizations handling sensitive data. Implementing an ISMS helps businesses meet these requirements and demonstrate their commitment to data protection.
Maintaining Customer Trust
Customers place a great deal of trust in businesses with whom they share their personal information. A data breach or security incident can severely damage a company’s reputation and erode customer trust.
Implementing an ISMS not only safeguards customer data but also demonstrates a commitment to security. By effectively managing information security risks, businesses can assure their customers that their data is in safe hands. This trust can translate into long-term customer relationships and a competitive advantage in the market.
Key Components of an Information Security Management System (ISMS)
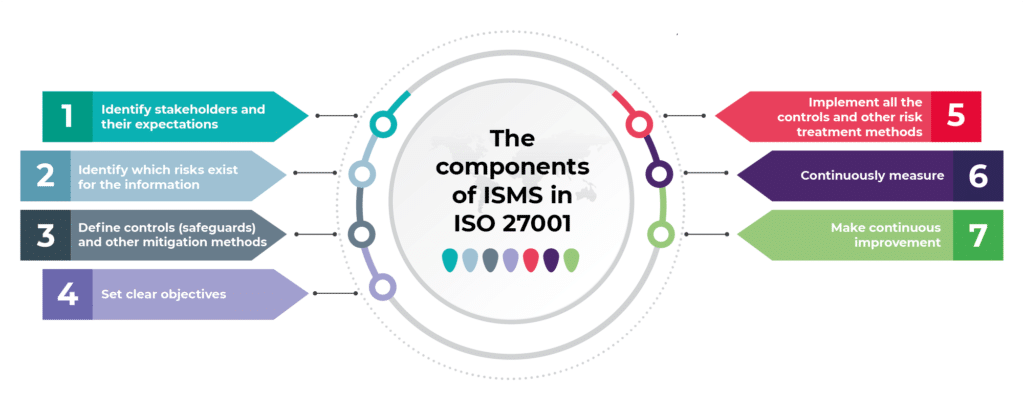
To establish a robust and effective ISMS, organizations need to consider several key components. These components work together to create a comprehensive security framework that addresses the unique needs and risks of the business. Let’s explore these components in more detail:
Risk Assessment and Management
A crucial aspect of an ISMS is the identification and assessment of information security risks. This involves conducting a thorough analysis of the organization’s assets, vulnerabilities, and potential threats. By understanding the risks, businesses can prioritize their security efforts and allocate resources effectively. Regular risk assessments help identify emerging threats and ensure that security measures are up to date.
Policies and Procedures
Clear and well-defined policies and procedures form the foundation of an ISMS. These documents outline the organization’s approach to information security and guide employees on how to handle sensitive data, use technology securely, and respond to security incidents. Policies should be regularly reviewed and updated to align with evolving threats and industry best practices.
Access Control and Authentication
Controlling access to sensitive information is vital for maintaining its confidentiality and integrity. An ISMS should include mechanisms for managing user access rights, enforcing strong authentication measures, and implementing appropriate access controls. This includes techniques such as user authentication, role-based access control, and encryption of data in transit and at rest.
Incident Response and Recovery
Despite best efforts, security incidents can still occur. An effective ISMS incorporates incident response procedures to detect, respond to, and recover from security breaches. This includes establishing incident response teams, defining escalation procedures, and implementing incident management processes. Organizations should have robust backup and recovery strategies in place to minimize the impact of incidents and restore operations promptly.
Employee Training and Awareness
Employees play a critical role in maintaining information security. They need to be aware of security policies, trained on best practices and educated about emerging threats. An ISMS should include regular training and awareness programs to ensure that employees understand their responsibilities and can actively contribute to the organization’s security posture.
Implementing an Effective Information Security Management System (ISMS)

Implementing an ISMS requires a structured and systematic approach. Here are some key steps to consider:
Establishing a Security Culture
Security should be ingrained in the organization’s culture and values. Top management should demonstrate a strong commitment to information security and set the tone for the entire organization. By promoting a security-conscious environment, employees will understand the importance of information security and be motivated to adhere to best practices.
Conducting Regular Risk Assessments
Regular risk assessments are essential to identify and prioritize potential security risks. This involves identifying assets, assessing vulnerabilities, evaluating the likelihood and impact of threats, and implementing appropriate risk mitigation measures. Risk assessments should be conducted periodically and whenever there are significant changes in the business environment.
Developing Robust Policies and Procedures
Clear and comprehensive policies and procedures serve as a guide for employees to follow. These documents should address various aspects of information security, including data classification, acceptable use of technology resources, incident response, and data retention. Policies and procedures should be communicated to all employees and regularly reviewed to ensure they remain relevant and effective.
Deploying Security Technologies
Implementing security technologies is crucial for protecting sensitive information. This may include firewalls, intrusion detection systems, encryption tools, antivirus software, and secure remote access solutions. Organizations should carefully select and configure these technologies to align with their specific security requirements.
Monitoring and Testing Security Controls
Regular monitoring and testing of security controls help identify vulnerabilities, detect unauthorized activities, and ensure compliance with established policies. This may involve conducting security audits, vulnerability assessments, penetration testing, and log analysis. By continuously monitoring and testing security controls, organizations can proactively identify weaknesses and take appropriate remedial actions.
Challenges in Implementing and Maintaining ISMS
While implementing an ISMS brings numerous benefits, organizations may face certain challenges:
Resource Constraints
Implementing and maintaining an ISMS requires dedicated resources, including financial investments, skilled personnel, and time commitment. Small and medium-sized enterprises, in particular, may face resource constraints when allocating budget and personnel to information security initiatives. However, organizations can prioritize their efforts and seek external assistance, such as outsourcing specific security functions or leveraging cloud-based security solutions.
Balancing Security and Usability
Striking the right balance between information security and usability can be challenging. Stringent security measures sometimes inconvenience employees or hinder productivity. Organizations need to find the right balance by implementing security controls that are effective yet user-friendly. User education and awareness can help employees understand the importance of security measures and adopt secure practices without impeding their work.
Keeping Up with Evolving Threats
The threat landscape is constantly evolving, with new vulnerabilities and attack vectors emerging regularly. Organizations need to stay updated on the latest threats and adapt their security measures accordingly. This requires continuous monitoring, threat intelligence sharing, and staying informed about industry trends and best practices. Regular training and awareness programs for employees can also help them stay vigilant and informed about evolving threats.
Ensuring Compliance with Regulations
Compliance with relevant regulations and standards can be complex and challenging. Organizations must stay abreast of changing regulatory requirements and ensure their ISMS aligns with applicable laws. This may involve conducting regular compliance audits, implementing specific controls, and documenting evidence of compliance. Engaging legal and regulatory experts can help organizations navigate complex compliance landscapes.
Best Practices for ISMS Success

To maximize the effectiveness of an ISMS, organizations should consider the following best practices:
Top Management Commitment
Leadership buy-in and support are crucial for the success of an ISMS. Top management should demonstrate a strong commitment to information security and allocate the necessary resources to implement and maintain the ISMS. They should also communicate the importance of information security to all employees and lead by example.
Involvement of All Employees
Information security is the responsibility of every employee. Organizations should foster a culture of security awareness and encourage active participation from all employees. This can be achieved through regular training programs, awareness campaigns, and ongoing communication about security policies and practices. Involving employees in risk assessment, incident response, and security improvement initiatives can also enhance the effectiveness of the ISMS.
Regular Audits and Reviews
Periodic audits and reviews are essential to assess the effectiveness of the ISMS and identify areas for improvement. Internal and external audits can help organizations identify gaps, vulnerabilities, and non-compliance with established policies and controls. Regular reviews of security incidents, risk assessments, and performance metrics can provide valuable insights to refine and enhance the ISMS.
Continuous Improvement
Information security is an ongoing process that requires continuous improvement. Organizations should establish mechanisms to gather feedback, analyze security incidents, and learn from past experiences. This feedback loop helps identify areas for enhancement and implement corrective actions. By embracing a culture of continuous improvement, organizations can adapt to evolving threats and maintain the effectiveness of their ISMS.
Conclusion
In today’s digital age, organizations face increasing threats to their sensitive information. Implementing an Information Security Management System (ISMS) is essential for protecting valuable data, ensuring compliance with regulations, and maintaining customer trust. By addressing key components businesses can establish a robust security framework. Achieving ISO 27001 certification further demonstrates a commitment to international standards and enhances reputation. Despite challenges, organizations can overcome resource constraints, strike a balance between security and usability, and keep pace with evolving threats. By following best practices organizations can effectively safeguard their information assets and mitigate security risks.
If you are looking to implement any of the Infosec compliance frameworks such as SOC 2 compliance, HIPAA, ISO 27001, and GDPR compliance, Impanix can help. Book a Free consultation call with our experts or email us at [email protected] for inquiries.
