In today’s data-driven landscape, organizations face increasing pressure to protect sensitive information. SOC 2, is a framework developed by the AICPA to assess and audit the security, availability, processing integrity, confidentiality, and privacy controls of service organizations. In this blog, we will explore what SOC 2 is, its importance, and the key provisions and requirements involved. Join us as we delve into this critical aspect of data security and compliance.
Contents
What Is SOC 2?
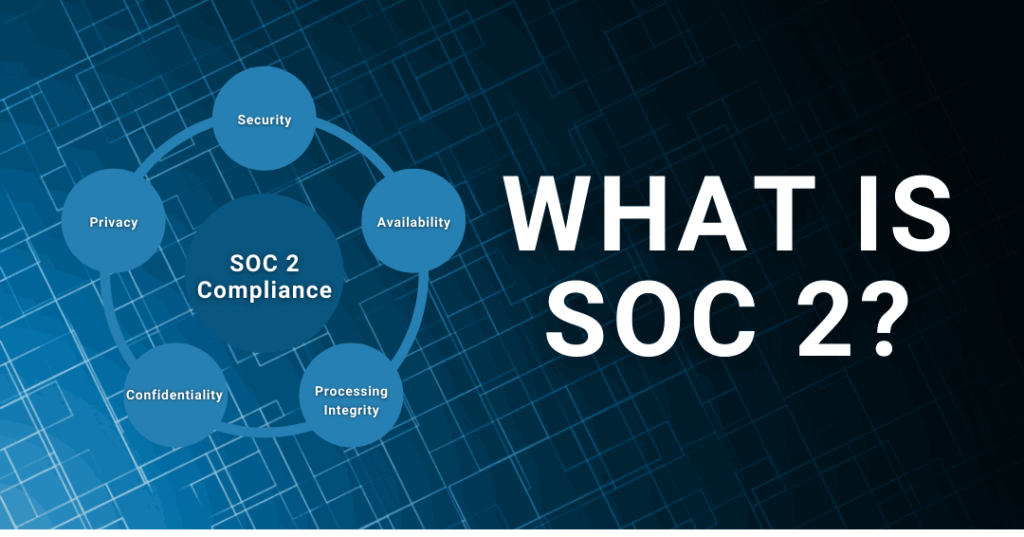
 SOC 2 (Service Organization Control 2) is a framework developed by the American Institute of Certified Public Accountants (AICPA) to assess and audit the security, availability, processing integrity, confidentiality, and privacy controls of service organizations. It is primarily used to evaluate the effectiveness of an organization’s systems and processes related to data security and privacy. SOC 2 reports assure customers and stakeholders about the organization’s adherence to industry best practices and compliance with relevant regulations.
SOC 2 (Service Organization Control 2) is a framework developed by the American Institute of Certified Public Accountants (AICPA) to assess and audit the security, availability, processing integrity, confidentiality, and privacy controls of service organizations. It is primarily used to evaluate the effectiveness of an organization’s systems and processes related to data security and privacy. SOC 2 reports assure customers and stakeholders about the organization’s adherence to industry best practices and compliance with relevant regulations.
Key Provisions In SOC 2
Organizations must meet some key provisions to demonstrate their compliance with the framework. These provisions include:
- Security: The organization must have adequate measures in place to protect against unauthorized access, ensure data confidentiality, and safeguard the systems and information it handles.
- Availability: The organization’s systems and services must be available and operational as agreed upon with customers, with minimal downtime or disruptions.
- Processing Integrity: The organization must ensure that its systems and processes are accurate, complete, and timely, ensuring the integrity of data processing.
- Confidentiality: The organization must maintain the confidentiality of sensitive information entrusted to it, both internally and externally.
- Privacy: The organization must handle personal information by the principles of privacy and have policies and procedures in place to protect individuals’ privacy rights.
SOC 2 audits assess the organization’s adherence to these provisions, assuring customers and stakeholders regarding the organization’s commitment to data security, availability, processing integrity, confidentiality, and privacy.
Who Does SOC 2 Apply To?
 SOC 2 applies to service organizations that provide services to other businesses or entities. This can include a wide range of organizations, such as cloud service providers, data centers, software-as-a-service (SaaS) providers, managed service providers (MSPs), and other service-oriented businesses.
SOC 2 applies to service organizations that provide services to other businesses or entities. This can include a wide range of organizations, such as cloud service providers, data centers, software-as-a-service (SaaS) providers, managed service providers (MSPs), and other service-oriented businesses.
These organizations handle and process sensitive information on behalf of their clients, making data security and privacy a critical concern. By obtaining a SOC 2 report, service organizations can demonstrate their commitment to implementing and maintaining effective controls in areas such as security, availability, processing integrity, confidentiality, and privacy.
What Are The Requirements For SOC 2?
To achieve SOC 2 compliance, organizations must fulfill several requirements and take specific actions. Here are some key elements required for SOC 2:
1. Implement Controls
Implementing controls involves developing and implementing policies, procedures, and measures that address the selected trust services criteria. For example, if security is one of the criteria, the organization may need to implement access controls, network security measures, data encryption, incident response procedures, and employee awareness training. These controls should be designed to mitigate risks and protect the systems and data involved.
2. Conduct Risk Assessment
It involves identifying and assessing potential risks and vulnerabilities associated with the organization’s systems and processes. The risk assessment helps determine the likelihood and impact of risks and allows the organization to prioritize and implement appropriate controls. By conducting a risk assessment, organizations can identify areas that require enhanced security measures or additional controls to achieve compliance.
3. Documentation and Evidence
 The organization should maintain comprehensive documentation that outlines its policies, procedures, and controls. This documentation demonstrates the organization’s commitment to compliance and provides evidence of the implemented controls during the audit process. Documentation can include control descriptions, risk assessment reports, incident response plans, training records, and other relevant documents.
The organization should maintain comprehensive documentation that outlines its policies, procedures, and controls. This documentation demonstrates the organization’s commitment to compliance and provides evidence of the implemented controls during the audit process. Documentation can include control descriptions, risk assessment reports, incident response plans, training records, and other relevant documents.
4. Independent Audit
SOC 2 requires an independent third-party audit conducted by a certified public accounting (CPA) firm or an external auditor. The auditor examines the organization’s controls and processes to assess compliance with the selected trust services criteria. The audit involves reviewing documentation, conducting interviews, and performing testing to evaluate the effectiveness of the controls. The auditor then prepares a report, providing an opinion on the organization’s compliance status. The organization can share this report with customers, stakeholders, and other relevant parties to assure the organization’s security and compliance efforts.
5. SOC 2 Reports
SOC 2 reports are an essential component of the SOC 2 compliance process. These reports provide detailed information about an organization’s controls and their effectiveness in meeting the selected trust services criteria. There are two main types of reports:
- Type 1: This report evaluates the design and implementation of an organization’s controls at a specific point in time. It provides an opinion on whether the controls are suitable to achieve the trust services criteria.
- Type 2: This report goes beyond the design assessment and includes an examination of the operating effectiveness of the controls over a specified period. It assesses whether the controls were operating effectively and meeting the trust services criteria throughout the assessment period.
These reports are valuable resources for customers, stakeholders, and regulators to evaluate the security, privacy, and compliance efforts of service organizations.
Why Is SOC 2 Important?
 SOC 2 is important for several reasons:
SOC 2 is important for several reasons:
- Trust and Assurance: SOC 2 provides an independent validation of an organization’s controls and practices related to data security, availability, processing integrity, confidentiality, and privacy. Hence, by obtaining a report, service organizations can assure their customers, stakeholders, and business partners that they have implemented effective controls to protect sensitive information.
- Compliance and Regulatory Requirements: It helps organizations meet industry-specific regulatory requirements. Moreover, it demonstrates their commitment to security and privacy standards mandated by regulations. Such as the HIPAA, PCI DSS, and GDPR.
- Competitive Advantage: SOC 2 compliance can provide a competitive edge in the marketplace. Many organizations, especially those in highly regulated industries or handling sensitive customer data, prioritize working with service providers who can demonstrate compliance. It can give them confidence in the security and reliability of their services.
- Risk Mitigation: It helps identify and mitigate risks related to data security and privacy. This can help organizations proactively identify vulnerabilities, address gaps, and strengthen their overall security posture.
- Customer Expectations: In today’s data-driven world, customers expect their service providers to prioritize the protection of their sensitive information. SOC 2 compliance demonstrates an organization’s commitment to meeting these expectations, fostering trust and confidence among customers.
- Vendor Due Diligence: Organizations that rely on third-party service providers often conduct due diligence to assess the security and compliance practices of these vendors. Hence, SOC 2 reports provide valuable insights into the service provider’s controls, allowing organizations to make informed decisions about partnering with them.
Conclusion
In conclusion, SOC 2 is a framework that assesses the security, availability, processing integrity, confidentiality, and privacy controls of service organizations. It ensures organizations meet industry standards, comply with regulations, and protect sensitive data. Achieving compliance builds trust, provides a competitive advantage, and mitigates risks. However, navigating the complexities can be challenging. If you need assistance with SOC 2 compliance, seek help from experienced professionals to ensure a smooth and successful implementation.
If you are looking to implement any of the Infosec compliance frameworks such as SOC 2 compliance, HIPAA, ISO 27001, and GDPR compliance, Impanix can help. Book a Free consultation call with our experts or email us at [email protected] for inquiries.