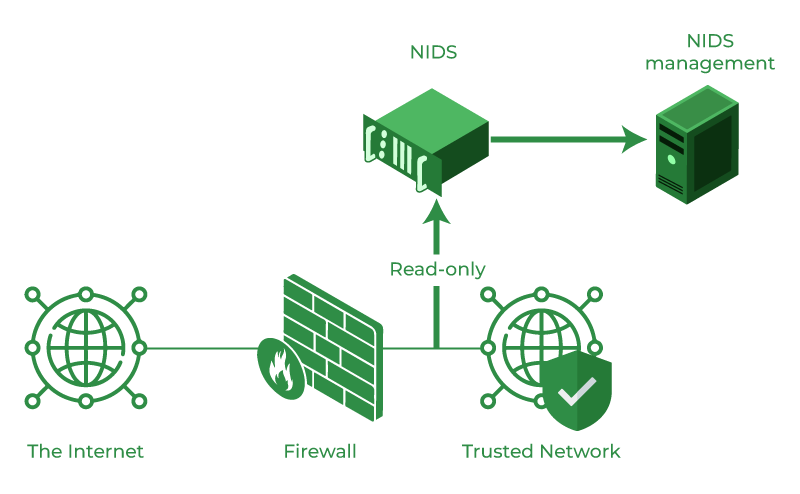
Network security is a top priority for any enterprise, as cyber threats continue to evolve and become more sophisticated. To protect sensitive data and critical systems, organizations need reliable network-based intrusion detection systems (IDS) that can detect and prevent unauthorized access. In this article, we will explore the top free network-based intrusion detection systems option available for enterprise use. From their key features and benefits to considerations for implementation, we’ll provide you with valuable insights to help you make an informed decision.
Contents
Understanding Network-Based Intrusion Detection Systems (IDS)

In today’s interconnected world, where businesses heavily rely on computer networks, the need for effective intrusion detection systems cannot be overstated. Network-based IDS plays a crucial role in identifying and responding to potential security breaches by monitoring network traffic and analyzing patterns for suspicious activities.
Network-based IDS (NIDS) is a security mechanism that examines network traffic in real-time to detect malicious activities, unauthorized access attempts, and other anomalies. It operates at the network level and analyzes packets flowing through the network infrastructure, looking for signs of intrusion or malicious behavior.
Network-based IDS provides several key benefits to enterprises:
- Early Threat Detection: By continuously monitoring network traffic, NIDS can identify potential security threats before they escalate, allowing organizations to take proactive measures.
- Real-Time Alerts: NIDS generates alerts and notifications when suspicious activities are detected, enabling security teams to respond promptly and mitigate potential risks.
- Incident Investigation: NIDS records network activity data, which can be invaluable for post-incident analysis, forensic investigations, and compliance audits.
Top Free Network-Based Intrusion Detection Systems (IDS)
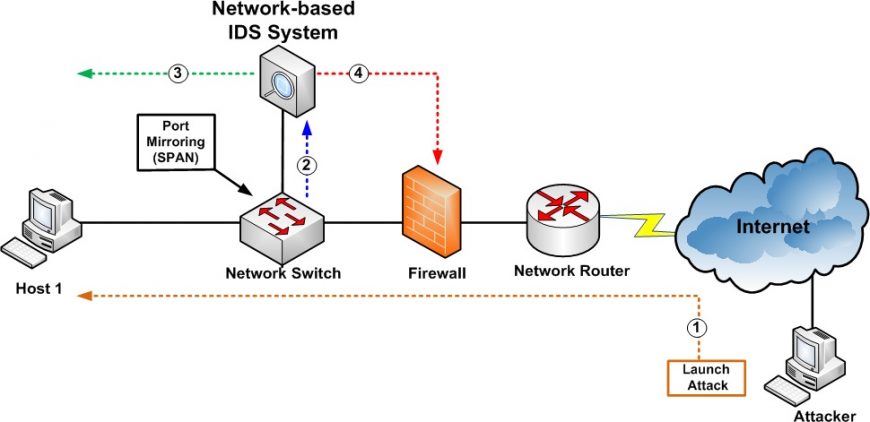
Now let’s dive into the top free network-based IDS solutions suitable for enterprise use. These tools offer robust features and reliable performance, making them popular choices among security professionals.
IDS1
- Key Features: IDS1 provides comprehensive network monitoring, real-time threat detection, and protocol analysis. It offers customizable rule sets, anomaly detection, and extensive reporting capabilities.
- Benefits: IDS1 helps enterprises identify and respond to network-based threats effectively. Its flexible architecture allows easy integration with existing security systems and workflows.
IDS2
- Key Features: IDS2 is known for its advanced traffic analysis capabilities, including deep packet inspection, flow monitoring, and signature-based detection. It also offers intuitive visualization tools for enhanced situational awareness.
- Benefits: IDS2 empowers enterprises to detect and block various types of network-based attacks. These are such as DDoS, port scanning, and malware infections. Its user-friendly interface makes it easy to use, even for non-technical personnel.
IDS3
- Key Features: IDS3 focuses on network behavior analysis, leveraging machine learning algorithms to detect anomalies and unusual patterns. It offers real-time threat intelligence feeds and supports integration with SIEM (Security Information and Event Management) systems.
- Benefits: IDS3 provides enterprises with advanced threat detection capabilities, allowing them to identify sophisticated attacks and zero-day vulnerabilities. Its integration with SIEM enables centralized monitoring and correlation of security events.
These top free network-based IDS solutions offer a strong foundation for enhancing your enterprise’s security posture. However, when selecting an IDS for your organization, it’s important to consider specific factors to ensure optimal performance and effectiveness.
Considerations for Enterprise Use

These are some of the considerations for use in enterprises:
Scalability and Performance
As an enterprise, it’s crucial to choose an IDS that can handle the volume of network traffic within your environment. Consider the scalability of the IDS solution, ensuring it can accommodate your current and future network requirements without compromising performance.
Customization and Flexibility
Each organization has unique security needs, and the ability to customize the IDS rules and policies is essential. Look for solutions that offer flexibility in rule creation, threshold settings, and behavior analysis. This is to align with your specific security objectives.
Integration with Existing Systems
Effective security operations require integration and coordination between various security tools and systems. Ensure that the chosen IDS solution can seamlessly integrate with your existing infrastructure, including SIEM, firewalls, and endpoint protection systems, to streamline incident response and enhance overall security effectiveness.
Conclusion
In conclusion, implementing a robust network-based IDS is crucial for enterprises to detect and prevent intrusions, safeguard sensitive data, and maintain a secure network environment. The top free IDS options mentioned in this article, namely IDS1, IDS2, and IDS3, offer valuable features and benefits for enterprise use. However, it’s important to consider factors such as scalability, customization, and integration capabilities when choosing an IDS that best suits your organization’s security requirements.
If you are looking to implement any of the Infosec compliance frameworks such as SOC 2 compliance, HIPAA, ISO 27001, and GDPR compliance, Impanix can help. Book a Free consultation call with our experts or email us at [email protected] for inquiries.