In today’s digital era, organizations are increasingly relying on third-party service providers to handle critical functions such as data storage, processing, and security. As businesses entrust their valuable data and operations to these service providers, the need for transparency, accountability, and assurance becomes paramount. SOC Trust Services Criteria, developed by the American Institute of Certified Public Accountants (AICPA), serve as a framework to assess and communicate the effectiveness of controls in service organizations. In this article, we will explore the significance of SOC Trust Services Criteria, its benefits, implementation challenges, and its role in cybersecurity risk management.
Contents
Understanding SOC Trust Services Criteria

The SOC Trust Services Criteria provide a comprehensive set of principles and criteria that service organizations must adhere to demonstrate the effectiveness of their controls. These criteria serve as a guide for service auditors to evaluate and report on the internal controls and processes of a service organization. The main purpose of this Trust Services Criteria is to assure stakeholders, such as clients, regulators, and business partners, assuredly, processing integrity, confidentiality, and privacy of the services provided by the organization.
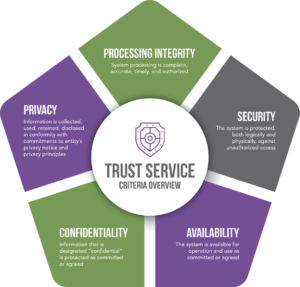
The SOC Trust Services Criteria are divided into five categories, each focusing on a specific aspect of the control environment:
- Security: This category assesses the protection of the system against unauthorized access, both physical and logical.
- Availability: It evaluates the availability of the system and the services it provides to users.
- Processing Integrity: This category ensures the accuracy, completeness, and timeliness of data processing.
- Confidentiality: It examines the protection of confidential information from unauthorized disclosure.
- Privacy: This category addresses the collection, use, retention, disclosure, and disposal of personal information.
Each category consists of multiple criteria that further define the specific requirements for achieving the desired control objectives.
Benefits of SOC Trust Services Criteria
Implementing SOC Trust Services Criteria offers several advantages for both service organizations and their stakeholders.
First and foremost, SOC reports provide assurance and trust to clients and other stakeholders. By obtaining a SOC report, service organizations demonstrate their commitment to maintaining strong internal controls and meeting industry best practices. This reassurance is particularly valuable in industries such as healthcare, finance, and IT, where data privacy and security are of utmost importance.
Secondly, SOC Trust Services Criteria contribute to enhanced risk management. By identifying and assessing potential risks and controls, organizations can strengthen their control environment, mitigate risks, and prevent potential incidents. The criteria serve as a benchmark for organizations to evaluate their control systems and make necessary improvements, resulting in a more robust risk management framework.
Additionally, SOC reports can help organizations comply with regulatory requirements. Many industries are subject to specific regulations regarding the protection of sensitive data and the implementation of adequate controls. SOC reports providing evidence of compliance with these regulations, making the audit process smoother and ensuring that organizations meet the necessary legal and industry standards.
Implementing SOC Trust Services Criteria

Implementing SOC Trust Services Criteria involves several key steps to ensure a thorough evaluation of controls and accurate reporting of findings.
Firstly, organizations should engage a qualified service auditor. Service auditors are independent professionals with expertise in evaluating control environments and issuing SOC reports. It is essential to select an auditor with relevant experience in the industry and a deep understanding of the specific SOC Trust Services Criteria applicable to the organization.
The next step is conducting a SOC audit. During the audit, the service auditor assesses the organization’s control environment, including policies, procedures, and technologies. They examine the design and operating effectiveness of controls to determine if they meet the criteria outlined in this Trust Services Criteria.
Once the audit is complete, the service auditor prepares a SOC report. The report details the findings of the audit and provides an opinion on the effectiveness of the organization’s controls. There are different types of SOC reports, including SOC 1, SOC 2, and SOC 3, each serving specific purposes and addressing different areas of focus.
SOC 1 vs. SOC 2 vs. SOC 3
SOC 1, SOC 2, and SOC 3 reports are different types of SOC reports, each designed for specific audiences and purposes.
Also, SOC 1 reports, also known as Service Organization Control (SOC) 1 reports, focus on controls relevant to financial reporting. These reports are often required by organizations that provide services that impact their client’s financial statements, such as payroll processing or financial transaction processing. SOC 1 reports assure the effectiveness of controls related to financial reporting organizations.
SOC 2 reports, on the other hand, assess controls related to security, availability, processing integrity, confidentiality, and privacy. These reports are intended for a broader audience, including clients, business partners, and regulatory bodies. SOC 2 reports are highly valuable for organizations operating in industries where data security and privacy are critical, such as healthcare, cloud services, and technology.
SOC 3 reports are summary-level reports that provide a general overview of the organization’s controls and their effectiveness. They are designed for public consumption and do not contain the detailed information found in SOC 2 reports. SOC 3 reports are often used as marketing tools, demonstrating to potential clients and stakeholders that the organization has implemented strong controls.
Challenges in Implementing SOC Trust Services Criteria
Implementing SOC Trust Services Criteria can present some challenges for organizations.
One common challenge is the complexity of the requirements. The criteria can be detailed and extensive, requiring organizations to invest time and resources in understanding and implementing them effectively. It is crucial to engage professionals with expertise in SOC audits to navigate the complexity and ensure compliance.
Cost implications can also be a concern. Conducting a SOC audit and obtaining SOC reports require a financial investment. Furthermore, organizations must allocate resources for engaging a service auditor, conducting the audit, and implementing necessary control improvements. However, the benefits of obtaining SOC reports often outweigh the costs, as they enhance trust and provide a competitive advantage in the market.
Another challenge lies in the need for continuous monitoring and updates. These Trust Services Criteria evolve to adapt to changing technology, risks, and regulatory requirements. Organizations must remain vigilant and stay up-to-date with the latest criteria to maintain the effectiveness of their controls and ensure ongoing compliance. Regular assessments and updates are essential to address new risks and maintain the relevance of the SOC reports.
Conclusion
Cybersecurity is a critical concern for organizations in today’s interconnected world. SOC Trust Services Criteria play a significant role in assessing and managing cybersecurity risks.
In conclusion, SOC Trust Services Criteria serve as a vital framework for assessing and communicating the effectiveness of controls in service organizations. They provide assurance, enhance risk management, and ensure compliance with regulatory requirements. By implementing SOC Trust Services Criteria, organizations can establish trust with their clients and stakeholders, strengthen their control environment, and demonstrate their commitment to data security and privacy.
If you are looking to implement any of the Infosec compliance frameworks such as SOC 2 compliance, HIPAA, ISO 27001, and GDPR compliance, Impanix can help. Book a Free consultation call with our experts or email us at [email protected] for inquiries.
