In today’s digital age, the security of our online communications and transactions is of utmost importance. Unfortunately, sophisticated cyber threats are lurking in the shadows, one of which is the Man-in-the-Middle (MITM) attack. In this article, we will delve into the details of MITM attacks, exploring their mechanisms, implications, and most importantly, how to safeguard ourselves against them.
Contents
What is a Man-in-the-Middle Attack?

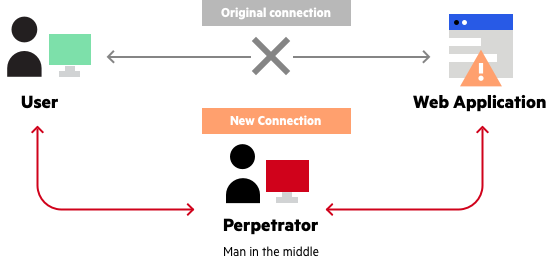
A Man-in-the-Middle attack is a malicious intrusion where an attacker secretly intercepts and relays communication between two parties who believe they are directly communicating with each other. The attacker positions themselves as an intermediary, intercepting sensitive data transmitted between the two unsuspecting parties.
How Does a Man-in-the-Middle Attack Work?
- Interception: The attacker gains access to the communication channel between the victim and the intended recipient.
- Impersonation: The attacker impersonates both parties, establishing connections with each independently.
- Eavesdropping: The attacker intercepts and collects data exchanged between the victim and the intended recipient without their knowledge.
- Manipulation: The attacker can modify or inject malicious content into the intercepted communication, leading to potentially devastating consequences.
Types of Man-in-the-Middle Attacks
- Wi-Fi Eavesdropping: Attackers exploit insecure Wi-Fi networks to intercept data transmitted over the network.
- ARP Spoofing: Attackers manipulate the Address Resolution Protocol (ARP) to redirect traffic to their own devices.
- DNS Spoofing: Attackers forge DNS responses, redirecting victims to fraudulent websites or servers.
- HTTPS Spoofing: Attackers create deceptive websites with fake security certificates to trick victims into revealing sensitive information.
Consequences of a Man-in-the-Middle Attack
The repercussions of falling victim to a MITM attack can be severe, including:
- Data Theft: Attackers can steal sensitive information, such as login credentials, financial details, or personal data.
- Identity Theft: By intercepting communications, attackers can assume the identity of victims, leading to fraud and unauthorized access.
- Financial Loss: MITM attacks can result in financial losses through fraudulent transactions or unauthorized access to accounts.
- Reputation Damage: Organizations and individuals can suffer reputational harm if their security measures are compromised.
Preventive Measures for Man-in-the-Middle Attacks

To mitigate the risks associated with MITM attacks, consider implementing the following preventive measures:
- Secure Network Infrastructure: Ensure that Wi-Fi networks and routers are properly configured with strong encryption and unique passwords.
- Use SSL/TLS: Websites and applications should implement SSL/TLS protocols to encrypt data in transit and verify the authenticity of servers.
- Two-Factor Authentication: Enable two-factor authentication whenever possible to add an extra layer of security to online accounts.
- Beware of Phishing Attempts: Stay vigilant against phishing attempts that could potentially lead to MITM attacks. Be cautious of suspicious emails, links, or attachments.
- Keep Software Updated: Regularly update your operating system, applications, and security software to patch vulnerabilities that attackers can exploit.
Best Practices for Protecting Against Man-in-the-Middle Attacks
- Verify Website Security: Before entering sensitive information on a website, ensure it has a valid SSL certificate and starts with “https” rather than “HTTP”.
- Use VPNs: Virtual Private Networks (VPNs) create secure tunnels between devices and networks, protecting data from interception.
- Exercise Caution on Public Wi-Fi: Avoid accessing sensitive information or conducting financial transactions on public Wi-Fi networks, as they are susceptible to MITM attacks.
- Regularly Monitor Accounts: Regularly check your financial and online accounts for any suspicious activity or unauthorized access.
- Educate Users: Raise awareness about the risks of MITM attacks and provide guidelines on safe online practices to prevent falling victim to such attacks.
Examples of Notorious Man-in-the-Middle Attacks
- Superfish: In 2015, it was discovered that certain Lenovo laptops were pre-installed with Superfish adware, which used MITM techniques to inject unwanted advertisements into users’ browsing sessions.
- Evil Twin Attacks: Attackers set up rogue Wi-Fi networks with similar names to legitimate ones, tricking users into connecting to them and intercepting their data.
- HTTPS Stripping: Attackers downgrade secure HTTPS connections to unencrypted HTTP, allowing them to intercept and manipulate data.
How to Detect and Respond to a Man-in-the-Middle Attack?

- Monitor Network Traffic: Analyze network traffic patterns and look for anomalies that could indicate a potential MITM attack.
- Pay Attention to Certificate Warnings: If your browser displays certificate warnings or errors when accessing a website, exercise caution and verify the authenticity of the certificate.
- Use Intrusion Detection Systems (IDS): Deploy IDS tools that can detect and alert you to any suspicious activity or unauthorized access attempts.
Conclusion
In an increasingly interconnected world, protecting ourselves from Man-in-the-Middle attacks is of utmost importance. By understanding the mechanisms behind these attacks, implementing preventive measures, and staying vigilant, we can significantly reduce the risks associated with MITM attacks. Secure communication channels, encryption, and best practices for online security play a vital role in safeguarding our sensitive information from falling into the wrong hands.
If you are looking to implement any of the Infosec compliance frameworks such as SOC 2 compliance, HIPAA, ISO 27001, and GDPR compliance, Impanix can help. Book a Free consultation call with our experts or email us at [email protected] for inquiries.